
Cyber Security Basics: Incident Response Team
Learn now about Incident Response Team, and how can it assist your organization in remediating cyber-attacks and emerging threats.
Initializing security protocols...
Explore 9 articles related to Information Security

Learn now about Incident Response Team, and how can it assist your organization in remediating cyber-attacks and emerging threats.

In this article we will explain the term “Red Team”, how does a Red Team Operation work and what are it’s benefits. Check it now.

Cyber criminals are taking advantage of the coronavirus crisis, people are distracted and much more vulnerable, everyone is at home practicing social distancing, using their electronic devices more than ever. Read more.

Red Team Operations services are just one of Scorpiones’s tools of raising an effective defense against Information Security Threats.

Kubernetes is a portable, extensible, open-source platform for managing containerized workloads and services, that facilitates both declarative configuration and automation. while docker is a Package Software into Standardized Units for Development, Shipment and Deployment

In this article we will help you understand what is GDPR, and more specifically, how GDPR relates to security and penetration testing.
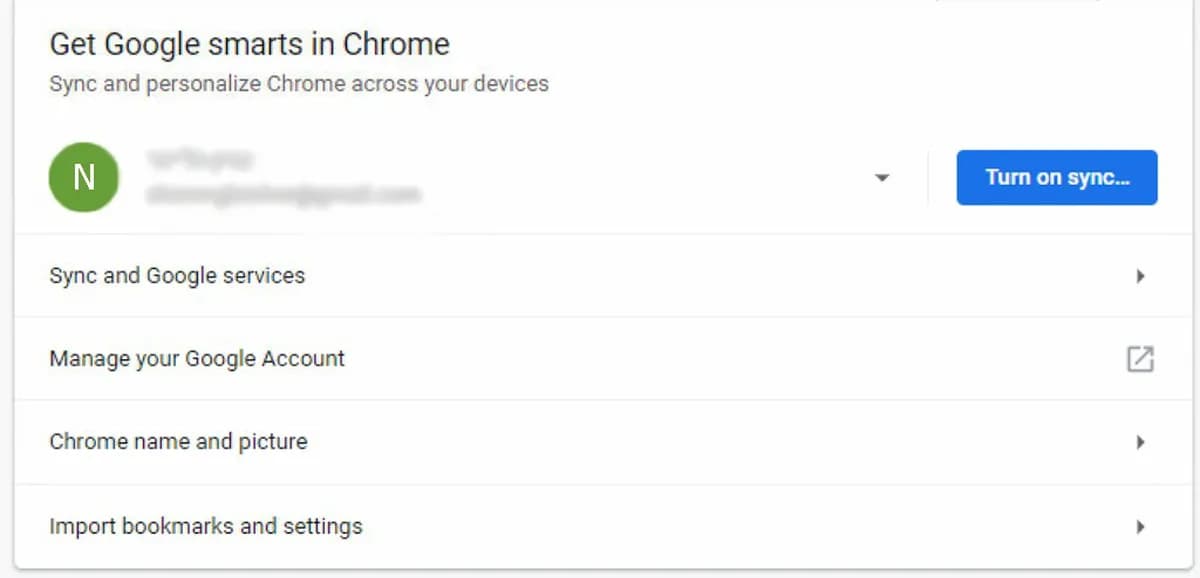
When you sign in to Chrome using your Google Account, a lot of your personal information gets saved and synced across all your devices, from an Information Security aspect, this is a nightmare.

Employees play a crucial role in running a successful business. An untrained and negligent workforce can put your enterprise in danger of multiple data breaches. Organizations must adopt an easy to accomplish security training program that should have the essential guidelines needed to stop Information Security Threats.

Requesting (and being given) permission for an app to perform operations that can provide access to user credentials, personal documents and images, personally identifiable or health information throws these resources open to abuse by cyber-criminals of all kinds. And permissions that grant an app deep system access are a great ruse for the installation of malware, spyware, and the hijacking of systems.